The Evolving Threat Landscape in 5G
Understanding the Shifting Sands of Cybersecurity
Cybersecurity is like a game of cat and mouse, with threats constantly changing shape and form. Organizations that fail to anticipate these shifts risk falling behind, leaving their systems exposed to novel attack vectors. Gone are the days when simple antivirus software could provide adequate protection.
Modern threats have evolved beyond basic malware. Attackers now employ psychological manipulation through social engineering, exploit previously unknown vulnerabilities, and leverage nation-state resources. Security teams must maintain continuous vigilance and education to counter these sophisticated tactics.
The Rise of Ransomware and Extortion
Ransomware has transformed from a nuisance to a serious business threat. Hospitals, schools, and government agencies have all fallen victim to these crippling attacks. The criminals behind them operate like professional businesses, often providing customer support for their victims.
The profitability of ransomware ensures its continued evolution, with attackers constantly refining their techniques. Organizations must implement multi-layered defenses, including offline backups and employee training, to mitigate these risks.
The Growing Importance of Zero Trust
The castle-and-moat approach to security is obsolete in today's distributed work environments. Zero Trust architecture represents a fundamental shift in security philosophy, requiring verification at every access attempt regardless of location or network.
The Impact of AI and Machine Learning
AI tools are revolutionizing threat detection, analyzing patterns at speeds impossible for human analysts. These systems can identify anomalies that might indicate a breach in progress, enabling faster response times.
However, malicious actors are also harnessing AI capabilities, creating more convincing phishing emails and developing malware that can adapt to defenses. This technological arms race shows no signs of slowing.
Supply Chain Vulnerabilities
Modern businesses rely on complex networks of suppliers and vendors, each representing a potential weak link. A single compromised component can provide attackers with a backdoor into multiple organizations.
Comprehensive supply chain security requires cooperation across industries, with shared threat intelligence and standardized security requirements for all partners.
The Human Factor and Social Engineering
Despite technological advances, people remain the most unpredictable security element. Clever social engineering can bypass even the most sophisticated technical controls.
Regular, engaging security training is essential to help employees recognize and resist manipulation attempts. Simulated phishing exercises can reinforce these lessons effectively.
The Need for Proactive Security Posture
Waiting for an attack to occur before responding is no longer viable. Modern security strategies must focus on prevention and early detection.
Continuous monitoring, threat hunting, and regular security assessments form the foundation of proactive defense. These measures, combined with a security-conscious culture, can significantly reduce risk exposure.
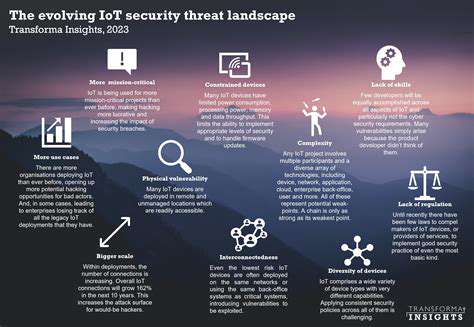
The Rise of IoT Devices and the 5G Ecosystem
The Expanding IoT Landscape
The Internet of Things continues its explosive growth, with estimates suggesting tens of billions of connected devices worldwide. These range from smart thermostats to industrial control systems, each presenting unique security challenges. Many IoT devices lack robust security features, making them attractive targets for botnets and other malicious activities.
The massive data streams generated by these devices create both opportunities and risks. Without proper safeguards, sensitive information could be intercepted or manipulated, with potentially serious consequences.
5G's Role in IoT Expansion
5G networks serve as the backbone for next-generation IoT applications. Their high-speed, low-latency characteristics enable real-time applications like autonomous vehicles and remote surgery. However, this increased connectivity also expands the potential attack surface.
The distributed nature of 5G infrastructure presents new security considerations. Network slicing, while offering benefits, requires careful implementation to prevent isolation failures between different service segments.
Security Concerns in the 5G-IoT Convergence
The combination of 5G and IoT creates complex security interdependencies. A vulnerability in one area could have cascading effects across the entire ecosystem. Device authentication becomes particularly challenging at scale, requiring innovative solutions.
Emerging technologies like blockchain may offer solutions for secure device identity management. Regardless of approach, security must be designed into these systems from the ground up rather than added as an afterthought.
Addressing the Need for Enhanced Security Protocols

Improving Security Protocols
Modern security protocols must balance protection with usability. Overly complex systems often lead to workarounds that undermine security. Multi-factor authentication has proven particularly effective, significantly reducing account compromise rates when properly implemented.
Regular penetration testing helps identify weaknesses before attackers can exploit them. These assessments should be conducted by independent third parties for maximum objectivity.
Enhancing Data Privacy
Privacy protections are increasingly important in an era of heightened regulatory scrutiny. Data minimization principles should guide collection practices, limiting information retention to only what's necessary for defined purposes.
Privacy-enhancing technologies like differential privacy allow valuable data analysis while protecting individual identities. These approaches will become increasingly important as data sharing grows.
Optimizing System Performance
Security measures should enhance rather than hinder system performance. Careful architecture can achieve both goals simultaneously. For example, properly configured caching can improve both speed and security by reducing attack surfaces.
Performance monitoring tools can detect security anomalies, as unusual resource usage often indicates malicious activity. This dual-purpose approach maximizes security investments.
Developing Secure Software
Secure development practices must become standard rather than exceptional. This includes regular code reviews, static analysis, and comprehensive testing. Security training for developers pays significant dividends in reducing vulnerabilities.
Automated vulnerability scanning should be integrated into CI/CD pipelines, catching issues early in the development process when they're easiest to fix.
Addressing User Education and Awareness
Effective security training goes beyond annual compliance requirements. Engaging, scenario-based learning helps employees internalize security principles. Gamification elements can increase participation and retention.
Clear communication of security policies prevents confusion and ensures consistent application across the organization. Regular updates keep security top-of-mind as threats evolve.
