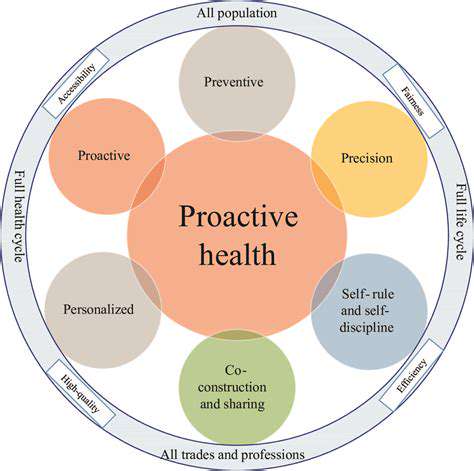
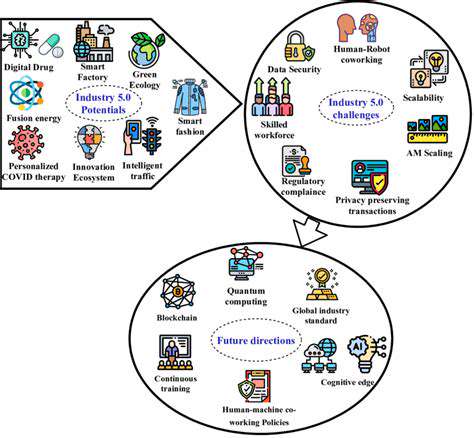
Streamlining Processes and Reducing Costs

Streamlining Processes for Enhanced Efficiency
Streamlining processes is crucial for any organization aiming to improve operational efficiency and productivity. By identifying and eliminating unnecessary steps, organizations can significantly reduce wasted time and resources, leading to greater profitability and a more positive bottom line. This efficiency boost translates into better customer service, faster turnaround times, and increased overall satisfaction.
A well-structured process ensures that tasks are completed in a logical and predictable manner. This predictability allows for better resource allocation and reduces the likelihood of errors, ultimately minimizing the risk of costly delays and rework. Optimizing workflows is paramount for achieving long-term organizational success.
Reducing Costs through Process Optimization
One key benefit of streamlined processes is the reduction of costs. By eliminating redundant steps and automating tasks, organizations can significantly reduce labor costs and material expenses. This cost reduction can be substantial, particularly in industries with high operational overhead.
Streamlining also reduces the potential for errors, which in turn minimizes the need for costly rework or corrections. This direct impact on cost reduction is a significant driver for businesses seeking to enhance their financial performance.
Improving Customer Satisfaction with Efficient Processes
Efficient processes directly impact customer satisfaction. Faster turnaround times, improved communication, and a more streamlined experience all contribute to a positive customer experience. Customers appreciate quick responses and clear communication, and efficient processes facilitate both. This positive customer experience is vital for building brand loyalty and driving repeat business.
When customers perceive a company as efficient and responsive, they are more likely to remain loyal and recommend the business to others. This positive feedback loop is crucial for long-term growth and success in today's competitive market.
Enhancing Communication and Collaboration
Streamlined processes often necessitate improved communication and collaboration between different departments. Clearer workflows and defined responsibilities ensure that information flows smoothly, reducing misunderstandings and delays. This, in turn, fosters a more productive and collaborative work environment.
Effective communication channels are essential for seamless information sharing and coordination. This is particularly important in a complex organization, where multiple departments or teams may be involved in a single process.
Increasing Productivity and Output
Improved efficiency directly leads to increased productivity and output. By removing bottlenecks and streamlining workflows, organizations can accomplish more in less time, boosting overall output and achieving greater return on investment. This increase in output is a direct result of optimized resource allocation and effective task management.
When processes are optimized, employees can focus on higher-value tasks, resulting in a more efficient and effective workforce. This leads to a more engaged and productive workforce, driving significant gains in overall output.
Adapting to Change and Maintaining Competitiveness
In today's dynamic business environment, organizations must be adaptable and responsive to change. Streamlined processes are crucial for facilitating change management and ensuring that the organization can swiftly adjust to new market conditions, customer demands, or technological advancements. This adaptability is paramount for maintaining a competitive edge.
Processes that are flexible and adaptable to change are more likely to withstand the pressures of market volatility. This ability to adapt and evolve is essential for long-term success in a competitive marketplace.
Mitigating Risks and Ensuring Authenticity

Identifying Potential Threats
A crucial first step in mitigating risks and ensuring authenticity is to proactively identify potential threats. This involves a thorough assessment of the environment, considering both internal and external factors. Internal risks might stem from employee negligence or malicious intent, while external risks could include cyberattacks, data breaches, or even natural disasters. Understanding these potential vulnerabilities is paramount to developing effective security measures. A comprehensive risk assessment should include detailed analysis of all operational processes and systems to highlight potential weaknesses.
Thorough research and analysis of the current security posture are essential for identifying potential threats. This involves examining existing security protocols, identifying gaps in protection, and understanding the potential impact of different threats. Regular audits and penetration testing can help uncover blind spots and improve overall security. Recognizing the specific ways malicious actors might target your systems or data will help strengthen defenses against attacks.
Implementing Robust Authentication Protocols
Robust authentication protocols are fundamental for verifying the identity of users and systems. Implementing multi-factor authentication (MFA) adds a critical layer of security, demanding more than just a username and password. This extra verification step significantly reduces the risk of unauthorized access, making it a vital component in any comprehensive security strategy. Strong passwords, combined with MFA, are a powerful combination against unauthorized access attempts. Regularly reviewing and updating authentication protocols can prevent known vulnerabilities from becoming points of exploitation.
Implementing strong password policies, including password complexity requirements and regular password changes, is critical. These policies should be consistently enforced across all user accounts. Educating users on best practices for creating and managing passwords is also essential to maintaining a strong security posture. Using strong, unique passwords minimizes the risk of unauthorized access to sensitive information through compromised accounts.
Enhancing Data Security Measures
Data security measures must extend beyond basic authentication. Data encryption, both in transit and at rest, is a fundamental requirement to protect sensitive information from unauthorized access. Employing strong encryption algorithms and protocols is vital for safeguarding data. Thorough data loss prevention (DLP) strategies are also crucial in preventing sensitive information from leaving authorized channels.
Regular data backups and recovery procedures provide a critical safety net in case of data loss or breaches. These procedures should be tested regularly to ensure their efficacy. Protecting data from unauthorized access is paramount, and robust encryption and backup strategies can significantly reduce the impact of security incidents. Additionally, regular security awareness training for all employees is essential for maintaining a strong security culture.
Establishing and Maintaining an Effective Security Culture
A strong security culture is essential for mitigating risks. This involves fostering a mindset where all employees understand and prioritize security. Clear communication of security policies and procedures is vital for ensuring everyone is aware of their responsibilities. Regular security awareness training programs can help employees recognize and avoid potential threats. Security training should be ongoing, not a one-time event, to stay abreast of emerging threats and best practices. Encouraging employees to report suspicious activity promptly can also help identify and address potential vulnerabilities quickly.
Establishing clear lines of communication and reporting channels for security concerns is important. This fosters a safe environment where employees feel comfortable raising potential issues without fear of retribution. A collaborative approach, where everyone is invested in maintaining a secure environment, is essential for a successful security posture. Regular security audits and reviews are crucial to identify vulnerabilities and update policies to maintain a strong security posture.