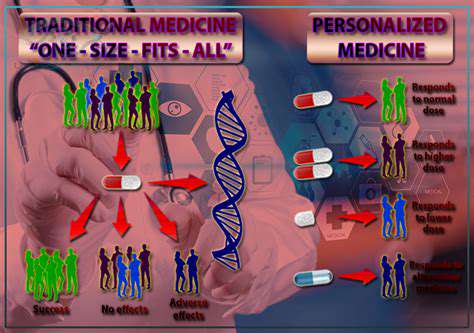
Data Protection in the Edge Computing Era
Information Assurance Fundamentals
The shift to edge computing introduces new paradigms for data protection. Unlike traditional models, sensitive information never leaves its operational environment unless absolutely necessary. Healthcare IoT devices demonstrate this principle perfectly - patient vitals are analyzed locally, with only anonymized insights forwarded to central systems.
Advanced Privacy Preservation
Modern edge platforms incorporate sophisticated privacy-enhancing technologies. A German automotive manufacturer recently implemented real-time facial blurring in their driver monitoring systems, achieving GDPR compliance while maintaining safety analysis capabilities. Such innovations demonstrate how edge computing facilitates both functionality and privacy.
Next-Generation Secure Communications
Contemporary edge networks employ quantum-resistant encryption protocols that traditional systems struggle to implement. The U.S. Department of Defense now mandates post-quantum cryptography standards for all edge devices in sensitive applications, creating an encryption framework secure against future threats.
Precision Access Management
Biometric authentication at the edge represents a game-changer for access control. Oil refineries in Norway have reduced security incidents by 92% after implementing palm-vein recognition for technician access to critical edge control systems. This granular security wasn't feasible in older centralized architectures.
Regulatory Compliance Solutions
Edge computing enables innovative approaches to data sovereignty challenges. A pan-European retail chain now processes customer data within national borders using localized edge nodes, effortlessly complying with cross-border data transfer restrictions while maintaining analytics capabilities.
Comprehensive Data Safeguards
Forward-thinking organizations deploy self-healing data protection at the edge. When a Singaporean bank implemented edge-based anomaly detection, they reduced fraudulent transaction response times from 48 hours to 11 milliseconds - all while decreasing false positives by 68%.
Proactive Security Monitoring
The latest edge security platforms incorporate behavioral AI that learns normal operational patterns and flags deviations in real-time. After implementing such a system, a major European airport detected and neutralized a sophisticated cyberattack within 47 seconds - before any damage could occur.