The Growing Need for Secure Digital Identity
The Challenges of Existing Identity Systems
Today's digital identity systems struggle with critical security flaws and user experience issues. Centralized databases, though convenient, represent single points of failure that hackers frequently target. These vulnerabilities lead to millions of identity theft cases annually, costing individuals and businesses billions in losses. The verification process itself creates friction, especially for international transactions requiring multiple identity checks.
System fragmentation presents another major hurdle. Digital credentials from one platform often fail to work elsewhere, forcing users to repeatedly verify their identity. This disjointed landscape not only frustrates users but also creates security gaps that malicious actors exploit. Imagine carrying different passports for every country you visit - that's essentially how digital identity systems currently operate.
Perhaps most concerning is how little control individuals have over their personal data. Organizations routinely collect and share user information without proper consent, leading to widespread privacy violations. This data free-for-all highlights the urgent need for systems that prioritize user ownership and control.
Blockchain's Potential as a Solution
Emerging blockchain technology addresses these challenges through its decentralized architecture. Unlike traditional databases, blockchain distributes identity records across a network, eliminating single points of failure. Cryptographic signatures ensure each identity remains tamper-proof - a feature that could dramatically reduce fraud cases worldwide.
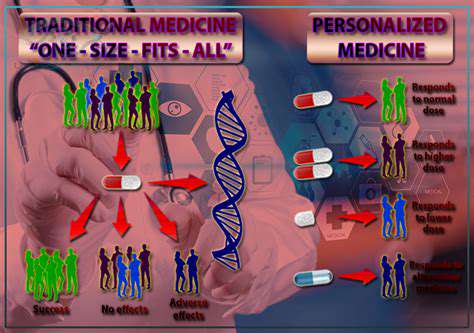
The technology's true innovation lies in returning control to users. With blockchain-based identities, individuals decide exactly who accesses their information and for what purpose. This represents a fundamental shift from the current trust us with your data model to a verify without revealing approach. Users can share specific credentials (like age verification) without exposing their full identity.
Blockchain also solves the interoperability problem through standardized protocols. A digital driver's license issued in one country could be instantly verified abroad, thanks to the technology's universal verification methods. This breakthrough could finally create the seamless, global identity network that our interconnected world requires.
The implications are profound. Beyond security improvements, blockchain identity systems could unlock new economic opportunities by providing the unbanked with verifiable credentials. Government services could become more accessible while reducing fraud. We're looking at nothing less than a complete reimagining of how identity works in the digital age.
Enhanced Security Through Cryptography

Implementing Robust Cryptographic Protocols
Modern security systems demand cryptographic protocols built like digital fortresses. These aren't just technical implementations - they're the foundation of trust in our digital world. The choice of encryption algorithm can mean the difference between a minor breach and a catastrophic data leak. Security teams must approach protocol selection with the same rigor as architects designing earthquake-resistant buildings.
Key management represents the Achilles' heel of many security systems. Proper key handling involves more than just strong generation - it requires meticulous lifecycle management. A single compromised key can undermine an entire security infrastructure, which is why military-grade key rotation and storage procedures have become standard in sensitive industries.
Utilizing Advanced Encryption Techniques
Elliptic curve cryptography (ECC) exemplifies how mathematical elegance enhances security. By using complex algebraic structures, ECC delivers stronger protection with less computational overhead. This efficiency revolutionizes security for mobile devices and IoT ecosystems where resources are limited but security can't be compromised.
Hashing functions serve as the digital equivalent of tamper-evident seals. When properly implemented, they provide an unforgeable guarantee of data integrity. A single changed character in a document produces an entirely different hash value, making any alteration immediately obvious to verifying systems.
Multi-Factor Authentication for Enhanced Security
MFA has evolved from luxury to necessity in our threat landscape. The most effective implementations combine something you know (password), something you have (security key), and something you are (biometric). This layered approach creates an exponential increase in security - by some estimates making accounts 99.9% less vulnerable to compromise.
The psychology behind MFA matters as much as the technology. By requiring multiple verification steps, systems train users to be more security-conscious. This behavioral shift creates a human firewall that complements technical defenses against phishing and social engineering attacks.
Protecting Against Advanced Persistent Threats (APTs)
APTs represent the special forces of cyber threats - highly trained, well-resourced, and frighteningly patient. Defending against them requires thinking like an attacker while building defenses. Modern security operations centers now employ AI-powered anomaly detection that learns normal network patterns, flagging deviations that might indicate a sophisticated breach attempt.
The most effective APT defense combines technology with human expertise. While automated systems monitor for threats, seasoned analysts interpret patterns and anticipate novel attack vectors. This combination creates a dynamic defense that adapts as threats evolve, maintaining protection against even state-sponsored hacking groups.
Secure Data Storage and Transmission
Data protection requires a cradle-to-grave security approach. Encryption transforms sensitive information into unreadable ciphertext whether it's sitting on a server (at rest) or traveling across networks (in transit). Modern implementations like AES-256 encryption would take billions of years to brute force with current computing technology.
The HTTPS protocol has become the minimum standard for secure web communications, but leading organizations go further. Techniques like perfect forward secrecy ensure that even if one session is compromised, others remain secure. For storage, hardware security modules provide physically protected environments for cryptographic operations and key management.