Harnessing Quantum Mechanics for Unbreakable Security

Quantum Computing: A Revolution in Computation
Quantum computing leverages the principles of quantum mechanics to perform calculations in a fundamentally different way than classical computers. This allows for the potential to solve complex problems currently intractable for even the most powerful supercomputers. This groundbreaking technology promises to revolutionize fields ranging from medicine to materials science. Quantum computers exploit quantum phenomena like superposition and entanglement, enabling them to explore multiple possibilities simultaneously, leading to exponential speedups in certain computations.
Superposition and Entanglement: Key Quantum Concepts
Superposition allows a quantum bit, or qubit, to exist in multiple states simultaneously, unlike a classical bit which is either 0 or 1. This inherent parallelism is a crucial aspect of quantum computation. Entanglement, another quantum phenomenon, links two or more qubits in such a way that they share the same fate, regardless of the distance separating them. This interconnectedness allows for intricate correlations and significantly enhances computational power.
Applications in Drug Discovery and Materials Science
Quantum computing's potential extends to drug discovery by enabling the simulation of molecular interactions with unprecedented accuracy. This can lead to the identification of new drug candidates and the optimization of existing therapies. In materials science, quantum simulations can predict the properties of new materials with tailored characteristics, enabling the design of stronger, lighter, and more efficient materials for various applications.
Challenges in Quantum Computing Development
Despite the immense promise, quantum computing faces significant technological hurdles. Building and maintaining stable qubits is incredibly challenging due to environmental noise and decoherence, which causes the qubits to lose their quantum properties. Developing robust error correction protocols is a critical area of research to ensure reliable quantum computations. Scaling up quantum systems to handle increasingly complex problems requires innovative engineering solutions.
Quantum Algorithms and Programming
Specialized quantum algorithms are crucial for leveraging the unique capabilities of quantum computers. These algorithms are designed to exploit superposition and entanglement to solve specific problems more efficiently than classical algorithms. Developing efficient quantum algorithms for a wide range of applications is a key focus in the field. Programming languages and software tools tailored to quantum computers are also necessary to effectively utilize their potential.
The Future of Quantum Computing
The future of quantum computing is bright, with ongoing research and development driving progress in various areas. Continued advancements in qubit technology, error correction, and algorithm design are expected to lead to more powerful and versatile quantum computers. The field is rapidly evolving, and the potential impact on numerous industries is poised to be transformative. Experts predict that quantum computing will play a significant role in shaping the future of technology and scientific discovery.
Quantum Key Distribution (QKD): The Core of Quantum Cryptography
Quantum Key Distribution (QKD): The Fundamentals
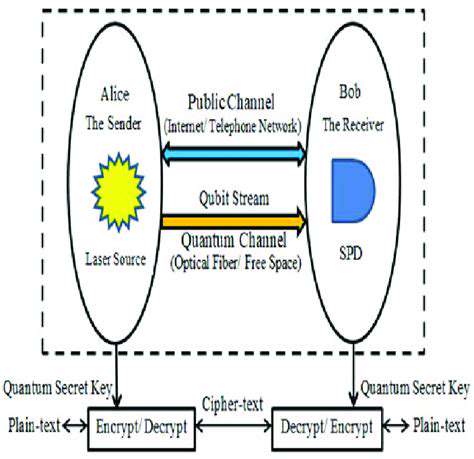
Quantum Key Distribution (QKD) is a revolutionary approach to secure communication, leveraging the principles of quantum mechanics to guarantee the secrecy of transmitted information. Unlike classical cryptography, which relies on mathematical assumptions, QKD leverages the fundamental laws of physics to guarantee the security of the key exchange process. This makes it inherently secure, as any attempt to eavesdrop on the key exchange would inevitably disturb the quantum state, alerting the legitimate parties.
The core principle behind QKD is that any attempt to measure a quantum system inevitably alters its state. This inherent property of quantum mechanics is used to detect eavesdropping and ensure that the shared key is truly random and secret. The quantum properties of photons, particularly their polarization, are employed to encode the key, making any attempt to intercept the key immediately detectable by the communicating parties.
Key Generation and Distribution Processes
The key generation process typically involves sending a stream of photons, each encoded with a specific quantum state, from one party (Alice) to another (Bob). These photons are carefully prepared and measured to ensure the desired level of security. This process is repeated many times to generate a sufficiently long key for encryption.
The distribution of the key is done over a quantum channel, often an optical fiber. The transmission of quantum bits (qubits) allows for the generation of a shared secret key known only to Alice and Bob. Simultaneously, they also establish a shared secret key, that can then be used to encrypt and decrypt messages using classical cryptography methods.
Security and Applications of QKD
QKD offers unparalleled security, as any attempt to intercept the quantum key will inevitably alter the quantum state, immediately alerting both Alice and Bob to the eavesdropping. This fundamental security is based on the laws of physics, making it impervious to advances in computing power or cryptographic algorithms.
Quantum Key Distribution has several potential applications in various sectors, including financial transactions, military communications, and government security. Furthermore, QKD can also contribute to secure data transmission in various other fields, such as healthcare and supply chain management, where the security of sensitive information is paramount.
The potential for QKD to secure critical infrastructures and sensitive information makes it a significant advancement in modern cryptography. Moreover, the ongoing research and development in this field promise even more robust and efficient QKD systems in the future.
Seafood, including salmon, tuna, and shrimp, offers a variety of essential nutrients beyond protein. These options provide omega-3 fatty acids, which are beneficial for heart health and brain function. The protein in seafood is easily digestible, helping your body quickly absorb the essential amino acids needed for optimal bodily functions.