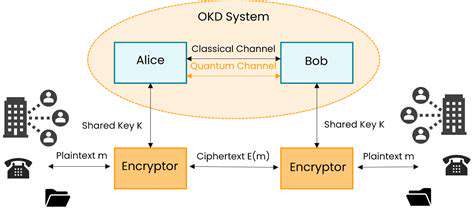
Quantum Key Distribution: The Core Principle
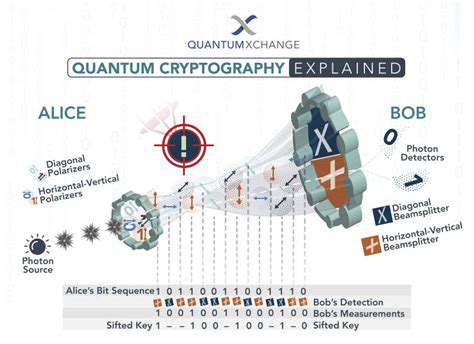
Quantum Key Distribution (QKD) leverages the fundamental principles of quantum mechanics to establish a shared secret key between two parties, known as Alice and Bob. This key is used for encrypting and decrypting messages, ensuring that any eavesdropping attempts are immediately detectable. Crucially, QKD relies on the inherent unpredictability of quantum phenomena, making it impossible for an adversary to intercept the key without being detected.
The core concept hinges on the idea that any attempt to measure a quantum system inevitably disturbs it. This intrinsic disturbance forms the basis for detecting eavesdropping. If an eavesdropper (Eve) tries to gain access to the key, her actions will alter the quantum state, alerting Alice and Bob to the intrusion.
Key Generation: Encoding Information in Photons
In QKD systems, information is encoded within the quantum properties of photons. These photons, fundamental particles of light, are transmitted between Alice and Bob. Different quantum states, such as the polarization or phase of the photons, represent the bits of the key. This encoding allows for the creation of a random, shared secret key between the two parties.
The process involves Alice preparing photons in specific quantum states, transmitting them to Bob, and Bob performing measurements to determine the corresponding bit values. This exchange creates a shared stream of random bits, forming the foundation for the secure key.
Quantum Entanglement: A Crucial Element
Entanglement plays a significant role in QKD. Entangled photons share an intrinsic link, meaning that the properties of one photon are correlated with the properties of the other, regardless of the distance separating them. This correlation is exploited in some QKD protocols to enhance security and efficiency.
The use of entangled photons allows for a more robust and efficient key distribution, as the correlations between the particles provide a powerful means of detecting any eavesdropping attempts by Eve. This entanglement-based approach is particularly relevant for long-distance communication.
Security Guarantees: Unbreakable Encryption
QKD offers a unique security guarantee that traditional encryption methods cannot match. The fundamental laws of quantum mechanics ensure that any eavesdropping attempt will be detectable. This inherent security stems from the impossibility of cloning an unknown quantum state, a concept known as the no-cloning theorem.
Any attempt to intercept and measure the photons will inevitably disrupt the quantum state, alerting Alice and Bob to the presence of an eavesdropper. This guarantees the secrecy of the shared key, making QKD a truly unbreakable encryption method.
Practical Implementation and Challenges
Implementing QKD systems presents practical challenges, including the need for specialized equipment and the susceptibility of quantum signals to noise and loss during transmission. The sensitivity of quantum signals to environmental factors necessitates careful design and implementation of the communication channels.
Furthermore, the distance over which QKD is effective is limited by factors such as atmospheric disturbances and the inherent attenuation of photons. Ongoing research focuses on improving the robustness and range of QKD systems to overcome these practical limitations.
Future Applications and Research Directions
QKD is not just a theoretical concept; it has the potential to revolutionize secure communication across various sectors. Future applications extend beyond traditional communication channels to encompass secure data centers, financial transactions, and national security systems.
Ongoing research is dedicated to improving the speed, efficiency, and range of QKD systems. Researchers are exploring new quantum states for encoding information, developing more sophisticated detection techniques, and investigating ways to mitigate the impact of environmental noise on the transmission of quantum signals.
Beyond Key Exchange: Applications of Quantum Cryptography
Beyond the Basics: Enhancing Security
Expanding beyond simple key exchange, modern cryptographic applications encompass a wide range of security needs. These applications involve not only the secure transmission of data but also the authentication of users, the integrity of information, and the non-repudiation of actions. Understanding these broader applications is crucial for building robust and secure systems. This involves a deeper dive into how cryptography is employed in diverse settings, from protecting sensitive financial transactions to verifying the authenticity of digital signatures.
The principles of key exchange, though foundational, are not the sole focus of modern cryptographic practice. Beyond the initial establishment of secure communication channels, sophisticated applications require mechanisms for secure data storage, access control, and verifiable computations. This necessitates a wider knowledge base and a more nuanced approach to implement comprehensive security solutions.
Digital Signatures and their Importance
Digital signatures are a critical aspect of modern security, providing authentication and non-repudiation. They ensure that a message originated from a specific sender and hasn't been tampered with during transmission. This is essential in many applications, including e-commerce, electronic voting, and legal contracts. The use of cryptographic hash functions and asymmetric encryption algorithms makes digital signatures highly reliable and verifiable.
Implementing digital signatures often involves a complex process of generating key pairs, signing messages, and verifying signatures. The security of these systems hinges on the robustness of the underlying cryptographic algorithms and the secure storage of private keys. Compromising a private key could lead to a significant security breach, making secure key management practices paramount. Furthermore, ensuring the integrity of the signing process is vital for preventing malicious tampering.
Cryptographic Hash Functions and their Applications
Cryptographic hash functions play a crucial role in ensuring data integrity and authenticity. Their ability to generate unique, fixed-size hash values for any input data, regardless of size, makes them indispensable for verifying the integrity of files, documents, and messages. These functions are also critical in password storage and blockchain technology, where ensuring the immutability of data is paramount.
By providing a checksum of the data, cryptographic hash functions allow verification that the data hasn't been altered during transit or storage. This capability is essential in protecting against unauthorized modifications and ensuring data reliability. Furthermore, their one-way nature makes them effective tools for password hashing, preventing the direct retrieval of user passwords from stored hashes.
Hash functions are also fundamental to blockchain technology, where they are used to create a chain of blocks with each block containing a hash of the previous block. This chain structure ensures the immutability of the data and is a key component in ensuring the security and transparency of blockchain transactions.
The use of cryptographic hash functions in various applications highlights their broad impact on data security and integrity. Their strong collision resistance and efficiency contribute to the robustness of many security protocols.
Prebiotics are non-digestible food ingredients that selectively stimulate the growth and/or activity of one or a limited number of beneficial bacteria in the colon, thus improving host health. Essentially, they are like fuel for the good bacteria in your gut, fostering a healthy microbiome. This healthy gut environment can have a positive impact on various aspects of your well-being. Prebiotics are found naturally in many foods and are also available as supplements.
Overcoming Current Challenges and Future Outlook
Current Security Vulnerabilities in Traditional Cryptography
Traditional cryptographic methods, while widely used, face significant vulnerabilities in the modern digital landscape. The increasing computational power of quantum computers poses a direct threat to widely-used encryption algorithms like RSA and ECC. These algorithms rely on the difficulty of factoring large numbers or solving discrete logarithm problems, but quantum algorithms like Shor's algorithm can potentially break these systems in polynomial time, rendering sensitive data vulnerable to eavesdropping. This poses a serious concern for secure communication channels, financial transactions, and data storage in the digital age.
Moreover, side-channel attacks exploit physical characteristics of the cryptographic implementations to recover secret keys. These vulnerabilities exist in hardware and software and are often difficult to detect and mitigate. The ever-evolving sophistication of these attacks necessitates continuous research and development of robust countermeasures, highlighting the need for a paradigm shift in security approaches.
Quantum Cryptography: A Paradigm Shift in Security
Quantum cryptography provides a fundamentally different approach to security, leveraging the principles of quantum mechanics to create unbreakable encryption schemes. By utilizing the principles of quantum entanglement and superposition, quantum cryptography ensures the integrity and confidentiality of communication channels against any eavesdropping attempt. This approach is intrinsically secure, as any attempt to intercept a quantum-encrypted message will inevitably disturb the quantum state, alerting the legitimate parties to the intrusion.
Key Distribution Protocols in Quantum Cryptography
One of the cornerstones of quantum cryptography is the secure distribution of cryptographic keys. Protocols like BB84 (Bennett-Brassard 1984) and E91 (Ekert 1991) utilize the principles of quantum mechanics to establish secret keys between two parties. These protocols rely on the fundamental laws of quantum physics, ensuring that any attempt to intercept the key distribution process will leave an irreversible mark on the quantum state, signaling the presence of an eavesdropper.
These protocols are designed to ensure that the key exchange is completely secure. Any attempt to measure the quantum state during the distribution process will alter the state, alerting the legitimate parties to the intrusion. This fundamentally different approach to security offers a robust solution against potential attacks, even from adversaries with access to powerful quantum computers.
Applications and Implementation Challenges of Quantum Cryptography
Quantum cryptography has the potential to revolutionize various sectors, from secure communication networks to financial transactions. Its application in secure data storage and secure cloud computing is particularly promising, offering a powerful tool for safeguarding sensitive information in the digital age. The potential for widespread adoption is significant.
However, implementation challenges remain. The technology is still relatively nascent, and the cost of quantum cryptographic devices can be prohibitive. Furthermore, the infrastructure required to support quantum communication networks is complex and expensive to establish. Overcoming these hurdles is crucial for realizing the full potential of quantum cryptography.
Future Outlook and Research Directions
The future of quantum cryptography is bright, promising a new era of secure communication. Ongoing research focuses on enhancing the efficiency and scalability of quantum key distribution protocols. Researchers are also exploring new applications of quantum cryptography in areas like secure authentication and distributed computing. The development of more robust and cost-effective quantum cryptographic devices will be critical for widespread adoption.
Continued advancements in quantum information science and the development of practical, real-world applications are essential for the successful integration of quantum cryptography into existing communication systems and infrastructure. This will likely involve collaboration between academia, industry, and government to drive innovation and address the practical challenges associated with deploying quantum cryptography at scale.
The Future-Proof Nature of Quantum Cryptography
Quantum Computing's Unwavering Potential
Quantum computing, a revolutionary field, promises to reshape the technological landscape in ways we're only beginning to comprehend. Its fundamental principles, based on the principles of quantum mechanics, allow for the processing of information in a fundamentally different manner than classical computers. This groundbreaking approach unlocks the potential to tackle problems currently intractable for even the most powerful supercomputers. This includes complex simulations in fields like materials science and drug discovery, potentially leading to breakthroughs in medicine and engineering.
The inherent advantages of quantum computation lie in its ability to explore multiple possibilities simultaneously, a concept known as superposition. This allows quantum algorithms to explore vast solution spaces, potentially solving problems far beyond the capabilities of classical computers. This capability has the potential to revolutionize industries across the board, driving innovation and progress in unprecedented ways.
Overcoming Existing Computational Limitations
Classical computers, while remarkably powerful, are ultimately constrained by their binary nature. They represent information as bits, which can either be a 0 or a 1. Quantum computers, however, utilize qubits, which can exist in a superposition of both 0 and 1 simultaneously. This inherent flexibility allows quantum computers to explore numerous possibilities concurrently, vastly accelerating the search for solutions to complex problems.
This ability to explore multiple states simultaneously is a crucial factor in overcoming the limitations of classical computation. Existing classical algorithms face significant challenges in handling exponentially growing datasets and intricate problems, but quantum algorithms can potentially address these challenges with surprising efficiency. This is particularly important in areas requiring high-speed processing and analysis of massive datasets, such as financial modeling and climate research.
The Expanding Scope of Applications
The applications of quantum computing extend far beyond the realm of theoretical physics. From drug discovery to materials science, finance to cryptography, the potential impact is profound. Quantum simulations can accelerate the process of designing new drugs and materials, leading to faster development cycles and potentially life-saving treatments. In the financial sector, quantum algorithms can optimize portfolios and enhance risk management, while in cryptography, quantum-resistant algorithms are crucial to secure future communications.
These applications promise to transform various industries, pushing the boundaries of what is currently possible. The potential for breakthroughs in these areas is immense, with quantum computing poised to revolutionize not just individual industries, but society as a whole. As the field matures, further breakthroughs and innovations in quantum computing will be inevitable.
Ensuring Future-Proof Solutions
The future-proof nature of quantum computing lies in its ability to address the limitations of current computational technologies. Quantum algorithms can be tailored to solve problems that are currently intractable for classical computers, paving the way for innovative solutions in various fields. This includes tackling challenges in areas like artificial intelligence, machine learning, and data analysis, where quantum techniques can significantly enhance performance and efficiency.
Investing in quantum research today is an investment in the future, ensuring that our solutions will remain effective even as technology advances. The development and implementation of quantum-resistant cryptography is crucial to protect sensitive data in the face of future quantum computing advancements, ensuring the continued security of digital infrastructures for years to come.